Description
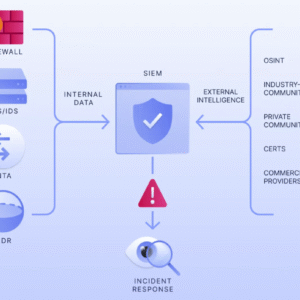
Cyber Deception Technology Setup equips your digital infrastructure with sophisticated decoy systems designed to detect attackers early in the breach process. We configure and deploy a mix of high-interaction honeypots, low-interaction decoys, fake credentials, dummy file shares, and decoy applications that simulate real assets—while silently monitoring intruder behavior. When attackers interact with these deceptive elements, your security team is alerted in real-time with rich telemetry. These insights allow you to observe attacker tools, TTPs (tactics, techniques, and procedures), and dwell time without risking production systems. This service supports integration with existing SIEMs and EDRs and is built on platforms like Canarytokens, T-Pot, or custom open-source stacks (e.g., Honeyd, Cowrie, Glutton). Ideal for high-security environments, this service turns your network into an active defense zone—confusing, delaying, and exposing attackers before they reach critical systems.



Doris –
Setting up the cyber deception technology with these folks was a surprisingly smooth experience. They clearly explained the benefits of using honeypots and other deceptive tactics, and their team expertly deployed a network of traps tailored to our environment. We’re already seeing promising results in identifying and understanding potential threats earlier in the attack chain. This proactive approach is giving us a significant advantage in strengthening our overall security posture.
Hani –
The cyber deception technology setup exceeded expectations. The implementation of honeypots and traps provided a valuable early warning system, allowing us to identify and respond to threats proactively. Their team demonstrated expertise and professionalism throughout the entire process, significantly improving our security posture.
Chigozie –
The cyber deception technology setup using honeypots and traps has significantly enhanced our security posture. The implementation was smooth and effective, providing early warnings of potential threats and enabling proactive responses. We now have greater visibility into malicious activity targeting our systems and are better equipped to protect our sensitive data.
Rabiu –
The cyber deception technology setup was incredibly effective. The implemented honeypots and traps have provided an invaluable early warning system, allowing us to identify and analyze potential threats before they could compromise our core network. This proactive approach has significantly enhanced our security posture and given us greater confidence in our ability to defend against sophisticated attacks.